Acknowledgment
These notes are based on the lectures and lectures notes of Srinivas Sampalli
for the class "CSCI-4174 Network Security". I attended this class in the
Winter 2024-2025 semester. If there are corrections or issues with these notes,
please use the contact page to let me know.
Review
Most of the review for this course is covered by my notes for Network
Computing.
Network Layers
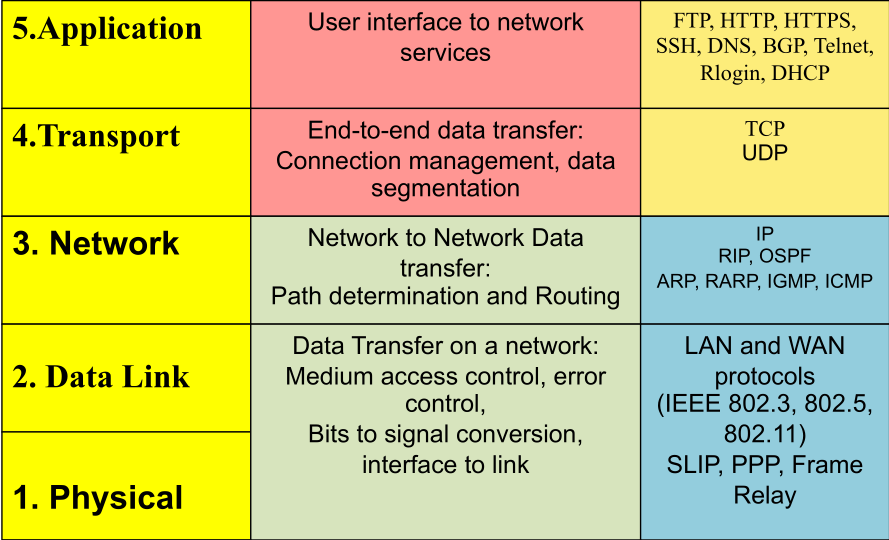
Typically the data link and the physical layers are implemented in hardware and
the rest are implemented in software.
Network Topologies
-
Point-to-Point: building block of all other topologies.
-
Linear: multiple point-to-point connection in a linear fashion. Data transfer
between nodes may need to go through other nodes, leading to poor fault
tolerance.
-
Bus: a linear topology, but all the nodes share a single link. We use
terminators to ensure that the signal isn't reflected. Transmissions may
collide and therefore we use the medium access control mechanism: carrier sense
multiple access with collision detection (CSMA/CD).
-
Ring: multiple nodes share a single link connected as a ring. Orderly
transmission without collision handled by token passing mechanism. The
token is a special bit pattern that rotates around the ring - only the node that
captures the token can send the message.
-
Dual Ring: increased fault tolerance version of ring topology.
-
Star: all nodes connected to a central hub which acts like a collapsed
bus. This is easier to install than the bus topology and has better fault
tolerance.
- In modern networks, the hub is replaced by a switch which only sends the
packet to the addressed node. This is called a switched ethernet connection.
- Mesh: multiple point-to-point links connected in an arbitrary topology.
This can either be a full mesh where every node is connected to every other
or a partial node.
Interconnection Devices
-
Hub/Repeater: boosts, cleans, and re-emits the signal received on any
port to all other ports. This only needs to access 1 of the stack (physical).
This is why they are called Layer 1 devices.
-
Switch: the switch is very similar to a hub but rather than sending the
received signal to all other connected nodes, it only send the data to the
node addressed in the packet. To do this, the switch needs to access layers
1-2 of the stack. This is why they are called Layer 2 devices.
-
Router: a router is used to connect different types of network
topologies. A router has multiple interfaces and each interface gets its own
IP address and MAC address. The connected networks must follow the same
protocol suites (e.g. TCP/IP). To do this, the router needs to access layers
1-3 of the stack. This is why they are called Layer 3 devices.
-
Gateway: a gateway is an interconnection device that connects networks of
different topologies and different protocol suites. Example, a gateway might
be used to connect a network running TCP/IP and DEC networks.
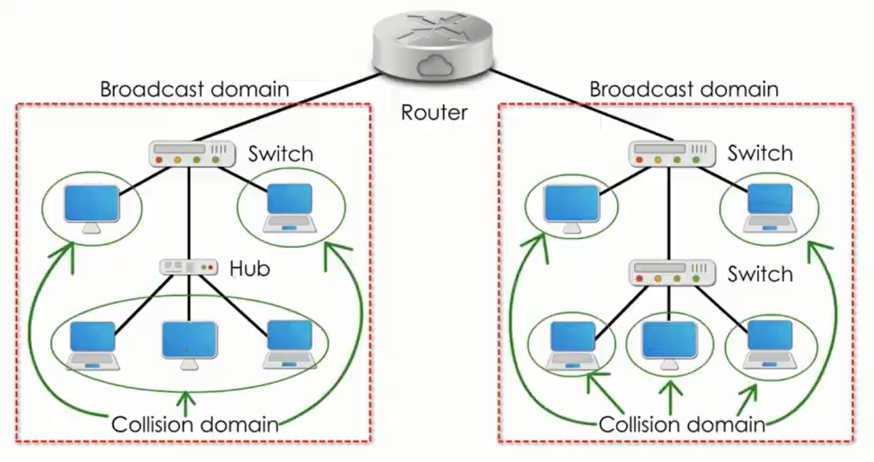
Collision and Broadcast Domains
A collision domain is the region in a network that a collision affect. That is,
if there is a collision on a particular wire, how much of the network does it
affect?
Repeaters or hubs are going to pass on the collision effects so they do not
separate collision domains. However, bridges/switches and everything above do
not propagate collisions and therefore, separate collision domains.
Routers separate LAN segments into different broadcast domains as a broadcast
messages doesn't propagate outside a router. Bridges forward all broadcast
messages.
Data Encapsulation
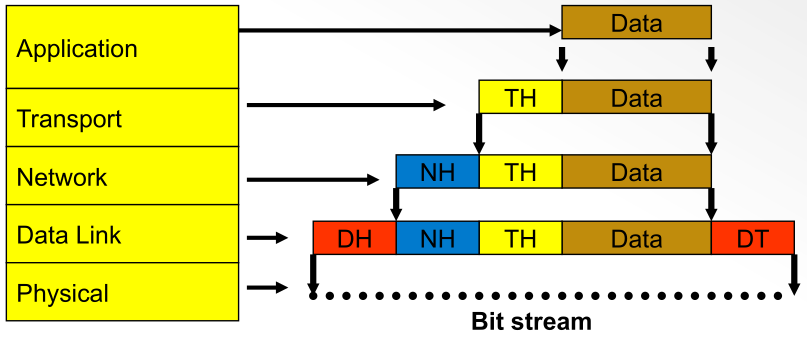
-
The application layer requests the data that needs to be sent to a different
machine on the network.
-
Segment: once the transport layer receives the data, it adds a transport
header (TH), which contains information such as the source and destination
port addresses.
-
Packet/Datagram: once the network layer receives the data, it adds a
network header (NH), which contains information such as the source and
destination IP addresses and the protocol ID.
-
Frame: Once the data link layer receives the data, it adds a data link
header (DH) and a data link trailer (DT). The DH contains type MAC addresses
and the type code. The DT holds the codes for error checking - cyclic redundancy
check (CRC check).
Addressing
Port Addresses
Port addresses are used to identify the application that sent the request.
Example, port 80 is usually an HTTP server.
- Standard ports \([0, 1023]\): standardized ports for protocols such as HTTP,
FTP, SSH, conventionally.
- Registered ports \([1024, 49151]\): ports usually reserved for 3rd party
applications like team-viewer and skype.
- Ephemeral ports \([49152, 65535]\): ports for dynamically sending requests.
Browsers use a random port in this range to create HTTP requests.
IP Addresses
These are used to identify machines globally and within networks. IP addresses
are 32 bit numbers usually written as 4 single-byte numbers - xx.xx.xx.xx.
-
Loop-back addresses: Addresses that are like 127.x.x.x are used to
identify services running on the same machine. Example: localhost refers
to the same machine and resolves to 127.0.0.1.
-
Broadcast addresses: Addresses that end with 255 like x.x.x.255 are
used to broadcast a message to all other nodes connected to the router.
-
Private addresses: These are addresses reserved for internal communication
within a local network. They are not routable on the public internet. The
common private IP ranges are:
-
10.0.0.0 to 10.255.255.255 are class A private networks.
172.16.0.0 to 172.31.255.255 are class B private networks.192.168.0.0 to 192.168.255.255 are class C private networks.
Devices using these addresses communicate internally but require NAT
(Network Address Translation) to access the internet.
- Public addresses: These are globally routable IP addresses assigned by
ISPs (Internet Service Providers). Devices with public IPs can directly access
and be accessed by the internet.
MAC Addresses
MAC (Media Access Control) addresses are unique identifiers assigned to network
interfaces for communication on the local network. They are 48-bit numbers
usually represented as six pairs of hexadecimal digits separated by colons or
hyphens (XX:XX:XX:XX:XX:XX).
-
Structure:
-
The first 24 bits (first three pairs) represent the Organizationally Unique
Identifier (OUI), which identifies the manufacturer of the network interface.
-
The last 24 bits (last three pairs) represent a unique identifier for the
device, assigned by the manufacturer.
-
Purpose: Unlike IP addresses, which can change based on network
configuration, MAC addresses are hardware-specific and remain constant. They are
used for addressing devices within a local network segment.
-
Example: 00:1A:2B:3C:4D:5E
-
Special MAC Addresses:
- Broadcast MAC Address:
FF:FF:FF:FF:FF:FF – used to send data to all
devices on the local network.
- Multicast MAC Address: MAC addresses starting with
01:00:5E are
reserved for multicast traffic.
- Locally Administered MAC Address (LAA): A MAC address where the second
least significant bit of the first byte is set to 1, indicating that the
address was manually assigned rather than factory-set.
MAC addresses ensure that data frames reach the correct physical device within a
local network.
Parsing Incoming Frame
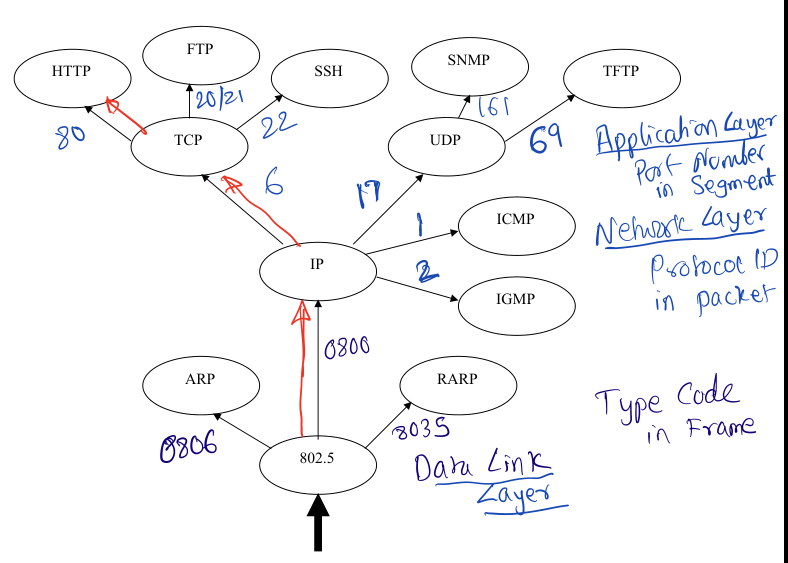
- At the data link layer, the
type code in the frame is used to decide between
ip, arp, rarp protocols.
- At the network layer, the
protocol id in the packet is used to decide between
tcp, udp, icmp, igmp protocols.
- At the application layer, the
port number in the segment is used to decide
between different applications.
Traceroute
traceroute uses a network management packet called an ICMP echo request
and manipulates a parameter called TTL (Time to Live) in the packet.
Typically, a packet starts with a TTL value of 64, which is decremented by 1 at
each hop (router) along its path. If the TTL reaches 0, the packet is discarded,
and the router that discards it sends an ICMP Time Exceeded message back to
the source. This mechanism prevents packets with incorrect or missing
destination addresses from endlessly circulating on the internet.
traceroute exploits this TTL behavior to map a packet's path. It first sends
an ICMP echo request with TTL set to 1. The first router discards it and replies
with an ICMP Time Exceeded message. traceroute then increases the TTL by 1
with each request, revealing each router along the path until reaching the
destination, which responds with an ICMP Echo Reply. For each reply it
receives, it measures the round-trip time.
Introduction
Terminology
- Vulnerability: Weakness in the network and/or its protocol.
- Threat: Set of circumstances that has the potential to cause harm.
- Intrusion: Any act or event that compromised the information on a network.
- Breach Breakdown of security of the network.
Hacker Types
-
Black Hat: Attack with malicious intent without authorization.
-
White Hat: Well-defined code of ethics and authorization focused on
improving security.
-
Gray Hat: Ambiguous ethics; often without authorization but without
malicious intent.
-
Blue Hat: Hired by tech companies to find product vulnerabilities.
-
Red Hat: Vigilante hackers who go after black hats; possibly hired by
government agencies.
-
Green Hat: student/amateur white hats who learn ethical hacking
techniques.
Intrusion Types
-
Interruption: Cause a resource to become unavailable to real clients.
Example: DOS.
-
Interception: Gain access to unauthorized access to information.
-
Active Eavesdropping: Hacker sends probes to access information.
-
Passive Eavesdropping: Hackers gathers information without sending probes.
-
Modification: Tampering with a resource or information and changing it.
-
Man-in-the-middle: modify the packets as they go from the server to the
client.
-
Fabrication: Insertion of counterfeit objects into a system. All malware
fall into this category.
-
Invasion: Taking control of a resource and stealing information.
-
Session Hijacking: the hacker "zaps" the client with a DoS attack and takes
over the connection to the server.
Levels Of Intrusion
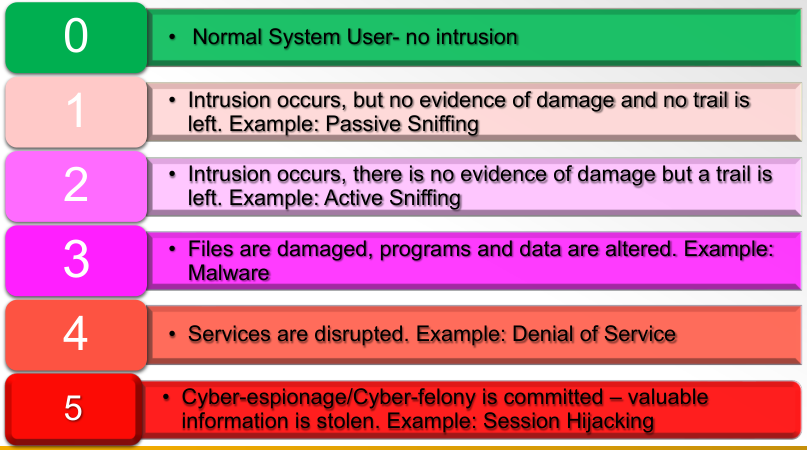
Anatomy of a Cyber Attack

-
Domains and subdomain information: what are the registered domains and
subdomains? What are the domain ownership details?
-
DNS records: find DNS Zone records such as A,AAAA,CNAME, MX, and name
servers.
-
IP addresses: what are the public-facing IP addresses and their ranges?
-
Servers: what services do the machines run? HTTP, FTP, SMTP, etc.
-
Open ports: what are the active ports and what services run of those ports?
-
Network and application infrastructure: what type of OS, CPU, firewall,
router, IDS, anti-virus, web technology is the victim running?
-
Publicly exposed documents: configuration files, source code, documents, etc.
-
Geo-location: what's the geographical location of the IP addresses and
servers, physical location of the network infrastructure such as wireless
access points.
-
Social media and public profiles: information about employees, system admins,
names, addresses, phone numbers, emails, voice prints, etc.
| Tool |
Purpose |
nslookup, dig, DNSDumpster |
Query domain names, DNS records, and IP addresses of name servers and end servers. |
sublist3r |
Enumerate sub-domains using search engines and other methods. |
whois |
Provide detailed domain information, including registration and contact details. |
Netcraft, WhatWeb |
Provide detailed information such as type and version of web server, associated technologies, geographical location, last update, etc. |
traceroute |
Map the IP addresses and determine round-trip times for each hop from the source to a destination. |
iplocation.net |
Find geo-location data for a domain name or IP address using tools such as ip2location, ipinfo.io, etc. |
nmap |
Port scanner to find active hosts, servers, and open ports. |
masscan |
A fast scanner for discovering open ports across a large range of IP addresses. |
shodan.io |
Discover exposed smart devices and their IPs. |
wireshark |
Capture traffic and analyze frames on the network. |
Netstumbler (Active Sniffer) |
Display MAC addresses of access points, SSIDs, channel numbers, vendors, and security status. It can also display location. |
Kismet (Passive Sniffer) |
Sniff out information similar to Netstumbler but passively. Can decloak hidden networks with SSID beaconing turned off. |
theHarvester |
Open-source intelligence tool that retrieves subdomains, hosts, IP addresses, emails, public documents, etc. |
recon-ng |
Comprehensive tool for gathering information similar to theHarvester. |
aircrack-ng |
Monitor, test, crack keys, and attack WiFi networks. |
Looking for Vulnerabilities
| Tool |
Purpose |
NESSUS |
Assess systems, networks, web applications, cloud services, malware detection and sensitive data searchs. |
Nexpose |
Detection, verification, risk calculation, impact analysis, reporting and mitigation |
GFILANguard |
Scans network IP by IP and alerts vulnerabilities. |
Netsparker |
Scan web servers and web applications and look for vulnerabilities as SQL injection, XSS, etc. |
Nipper Studio |
Vulnerability assessment scanner for switches, routers, and firewalls. |
MetaSploit |
Full suite of tools for gathering information, looking for vulnerabilities and running exploits. |
Gaining Access
Password Crackers
Tools like hashcat, RainbowCrack, JohntheRipper allow you to brute-force
and dictionary attack passwords and usernames.
Since most sites block repeated login attempts,the recover passwords from
encrypted files downloaded from breached servers.
Keyloggers
Another way of getting username and password is by installing keyloggers on the
victims computer. A keylogger records keystrokes and all the activity of the
user on whose machine it gets installed, and transfers all the information to a
remote site.
There exist both software-based keyloggers (malware) and hardware-based (USB
key) keyloggers.
Address Spoofers
Try to access a network by sending a packet/frame with spoofed legitimate IP/MAC
addresses. hping is a tool that allows you to send packets with spoofed IP
addresses. smac is a tool to spoof MAC addresses.
Launch Attack
DoS Attacks
The objective of a DoS attack is to bring down a network so that legitimate
users cannot access it. A common type of DoS is the Distributed Denial of
Service (DDoS) in which the target network is attacked from multiple sources
simultaneously.
Eavesdropping
Watch and capture traffic between a server and a client.
Man-in-the-Middle (MITM)
The hacker positions themselves between the client and the server. They pretend
to be the server to the client and the pretend to be the client to the server.
This is done by spoofing the IP address. Traffic will now flow through the
attacker's machine without the knowledge of the client or the server.
This can be extended to modify the data being sent by adding/dropping/modifying
the packets in transit.
Session Hijacking
The hacker watches ongoing communication between a client and a server and
records the session numbers, IP addresses, etc. Then, the attacker DoS attacks
the client and takes over the existing connection by spoofing the client to the
server using the same addresses, session numbers, etc.
Reply Attack
The hacker watches an ongoing communication and records the transaction and
replays the recorded packets to the server later.
"This works when the server does not save state information." (not necessary but
helps)
For example, before cars implemented rolling codes, a hacker could capture the
codes sent from your key fob to the car and then just replay same codes later to
unlock the car.
Security Goals
- Protect the network: Firewalls!
- Protect the transaction: Cryptography!
Our main security goals that we want to achieve:
| Security Goal |
Meaning |
| Confidentiality |
No eavesdropping |
| Integrity |
No alteration. Message received = Message sent |
| Authentication |
Sender validation. You are who you say you are. |
| Non-Repudiation |
Source cannot deny a transaction later. |
| Certification |
A third party certifies the source as trustworthy. |
| Access Control |
Who can access what and when. |
| Availability |
System resources are always available to legitimate users. |
The first five: confidentiality, integrity, authentication, non-repudiation,
certification are achieved through cryptography. The last two: access
control, and availability are achieved through firewalls.
Denial Of Service
The objective of a DoS attack is to disable a system or degrade its performance.
It prevents legitimate users from accessing a resource.
DoS is considered a nasty attack as it's one of the easiest attacks to launch
and it is very hard to trace the attacker. The response to a DoS attack usually
results in shutting down the network, a self-inflicted DoS.
The motivations for a DoS attack:
- recognition in the underworld community
- politically motivated - individuals or groups who disagree with views or
actions of a certain organization
- competitive edge - when a company wishes to gain a financial edge over its
competitors.
- extortion - online businesses are threatened with a DoS and a payment is
requested for protection.
Classification of DoS
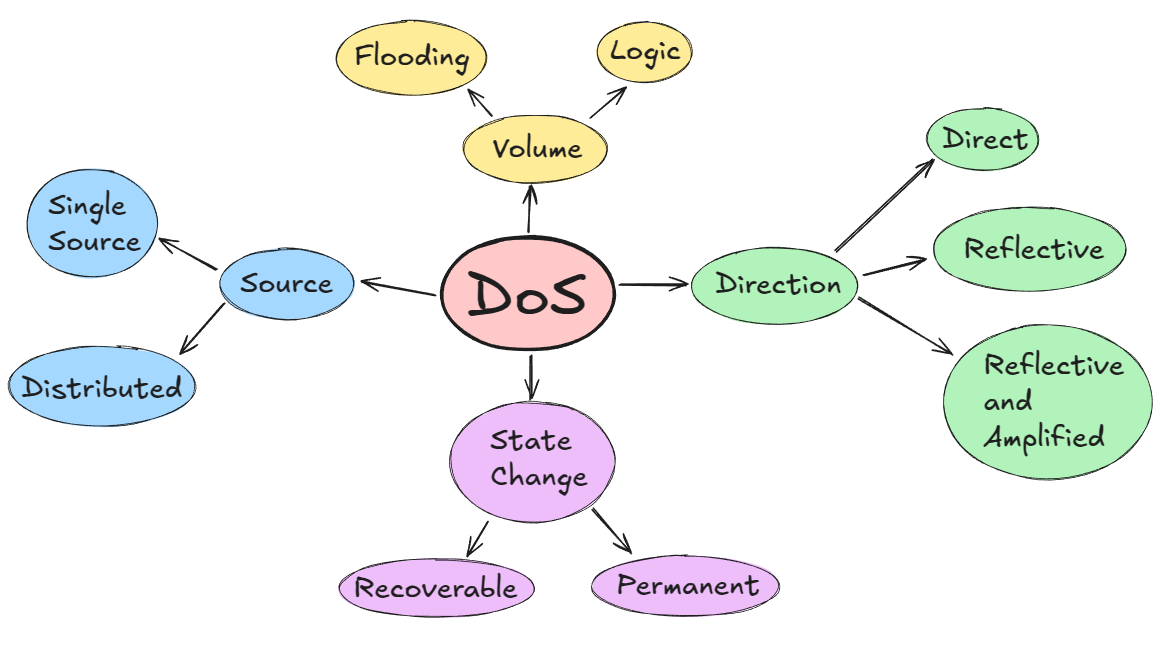
-
Volume
-
flooding: overwhelm with flood of data
-
logic: exploit vulnerabilities of target intelligently
-
Source
-
single: attacker uses a single machine
-
distributed (DDoS): DoS simultaneously launched from multiple sources.
-
Direction
-
direct: directly from attacker machine
- reflective: intermediary devices used for attack
-
reflective and amplified: like reflective but traffic is amplified by
intermediary devices (either in size of volume).
-
State
-
permanent dos: attacker disables system permanently, usually by destroying
firmware.
- recoverable: system can be recovered once the DoS attack ends or if the
system is rebooted.
Techniques
Ping Flood
Simple flood of ping packets to machine. ping <address of target>. The default
size is 64 bytes but the -s option can be used to change size and -i to
change the interval in seconds.
TCP SYN Flood
The TCP operation consists of a 3-way handshake:
- Connection request with the
SYN segment.
- Acknowledge with the
SYN-ACK segment.
- Acknowledge the
ACK with an ACK segment.
In the TCP SYN attack, we simply exploit this by only sending TCP SYN packets
with spoofed IP addresses without sending the ACK segments. The server usually
waits for about 3 minutes before closing the connection. This cases there to be
a lot of half-opened TCP connections, thus causing a DoS.
Land Attack
The attacker sends a TCP SYN segment that has been tweaked such that the
source IP, the destination IP are both set to the victim's IP address. If not
protected against, the victim will open empty TCP connections with itself.
The attacker sends a large number of such requests to DoS the server.
Other TCP Attacks
-
SYN-ACK Flood: Keep sending ACK segments to the victim from a spoofed
server.
-
Fragmented ACK Flood: Fragment ACK segments and flood the server. As
routers do not reassemble fragmented packets, they pass through such devices
(and some firewalls.)
-
RST or FIN Flood: Keep sending RST or FIN segments to the server.
Tear Drop Attack
The maximum size of an IP packet is 65,535 bytes while the maximum size of an
Ethernet frame is only 1500 bytes. Therefore, when an IP datagram of size
larger than 1500 reaches an Ethernet path, it has to be fragmented and then
reassembled at the destination.
In the tear drop attack, the attacker repeatedly fragments IP packets, sends all
but one fragment in each packet to the destination.
Ping Of Death
Quite simply, the attacker sends one oversized malformed ping packets that
larger than 65,535 bytes by fragmenting it. When the receiver tried to
reassemble the oversized packet, it would case the data link layer buffer to
overflow and possibly freeze, crash, or reboot.
Smurf Attack
The attacker sends a broadcast ICMP echo request to a network with a spoofed IP
address to be the victim's IP address. This will result in all the hosts on the
network sending ICMP echo replies to the victim.
This is an example of a reflective attack.
Routers block broadcast messages so smurf attacks are mostly mitigated on
current networks if launched from outside. However, some older routers pass
broadcast messages and such networks can be vulnerable.
Furthermore, if the smurf attack can be released by a malware from inside the
network, it can be successful.
UDP Flood Attacks
Attacker sends UDP packets to random ports on the victim's machine. When the
victim receives this, it sends a "ICMP destination unreachable" reply since
there is (probably) no application on this port.
If a large number of such UDP packets are sent on different ports, the victim
machine will be overloaded trying to determine if there are awaiting
applications and then generating and sending ICMP replies.
HTTP Verb Attacks
HTTP methods include GET, POST, PUT, DELETE. DoS attacks can send the
target HTTP servers using these methods.
- The Excessive VERB attack: generates a large number of valid GET requests
for a single page.
- Multiple VERB Single Request: a single packet with multiple GET requests.
- Recursive GET: Attacker generates a packet with a recursive GET requests
to traverse multiple pages on a website.
Reflection and Amplification Attacks
There exists many publicly accessible servers. These include DNS (Domain Name
Servers), NTP (Network Time Protocol), SSDP (Simple Service Discovery Protocol),
SNMP (Simple Network Management Protocol) v.2, BitTorrent.
The attacker sends a request with the spoofed IP address of the victim. Many
such requests can result in amplified replies The servers reflect their replies
to the victim.
| Protocol |
Bandwidth Amplification Factor |
Vulnerable Command |
| DNS |
28 to 54 |
Multiple |
| NTP |
556.9 |
Multiple |
| SNMPv2 |
6.3 |
GetBulk request |
| NetBIOS |
3.8 |
Name resolution |
| SSDP |
30.8 |
SEARCH request |
| CharGEN |
358.8 |
Character generation request |
| QOTD |
140.3 |
Quote request |
| BitTorrent |
3.8 |
File search |
| Kad |
16.3 |
Peer list exchange |
| Quake Network Protocol |
63.9 |
Server info exchange |
| Steam Protocol |
5.5 |
Server info exchange |
Source: US-CERT.
Botnet Based DoS Attacks
The DoS attack is launched by bots that are controlled (and/or compromised) by
the attack (usually using malware) and controlled by a command and control
server.
- Low Orbit Ion Cannon (LOIC): generate junk TCP, UDP, and HTTP traffic.
- High Orbit Ion Cannon (HOIC): an advance version of LOIC which floods web
servers with HTTP GET and POST requests.
- R. U. Dead Yet (R.U.D.Y): crawls the victim's web page to find forms, then
starts submitting form data at a very slow rate.
- SlowLoris: opens multiple simultaneous connections on a web server and
keeps them open for as long as possible. Sends partial HTTP requests at a very
slow rate, sending incomplete HTTP headers. Mainly affects Apache servers.
Detailed information on DoS tools:
Mitigation
- Traffic Monitoring: establish baselines for the system and detect abnormal
behaviour.
- Egress Filtering: match incoming ICMP replies with outgoing ICMP requests.
- Patch software: patch against known DoS attacks.
- Over provision bandwidth: accommodate sudden and unexpected increases in
traffic.
- DoS Mitigation Services: Special purpose device or service that
scrutinizes inbound traffic before it hits firewall. Distributed cloud
scrubbing centers like Prolexic, CloudFlare, Akamai.
Social Engineering
Tricks
- Impersonation: impersonate someone trustworthy or someone in authority.
- Ingratiation: appeal to vanity; use subtle flattery to get information.
- Friendliness: appeal to the human nature - people generally trust others
and want to be helpful.
- Fear and Urgency: push for immediate action.
- Diffusion of responsibility: make targets less accountable - e.g. "your
colleague has already given me their information".
Techniques
-
Dumpster Diving: huge amounts of sensitive information can be found in
dumpster as they aren't usually carefully disposed.
-
Phone: call up, imitate someone in authority and gradually extract information
from the victim.
-
Shoulder Surfing: watch over victims shoulders to get information about
usernames, passwords, etc.
-
Baiting: relies on human curiosity/greed/shock factor. Examples:
-
put up posters with QR codes at public places, inviting people to visit
fraudulent websites and provide information.
-
leave physical media labeled with sensitive information, for example, a USB
key marked "Company XYZ intellectual property files" is left in a public
area.
-
Pretexting: scammers call unsuspecting home PC users, pretend to find and
fix malware, but install malware.
-
Phishing: scam emails, making people click links.
-
Pharming: phishing without a lure, redirect to fraudulent by altering
hosts file or DNS poisoning.
-
Phlashing: permanent denial of service attack by exploiting firmware
upgrades. Deliver corrupted firmware and flash this to the device.
-
Spear Phishing: targeted phishing attacks on specific individuals or
organizations.
-
Credential Harvesting: obtain credentials in large numbers, example, an
insecure online form in which the user would enter username and password.
-
Hacking social media accounts: con friends of victim using their social
media account.
-
Reverse Social Engineering (RSE): rather than the attacker approaching the
victim, the victim is tricked into contacting the attacker. This enhances the
level of trust and encourages the victim to reveal more information.
IP Addresses
An IP address is a unique identifier assigned to each device (interface) in
a network. It consists of 32 bits (4 bytes) and is divided into two main
components:
- Network ID: Identifies the specific network.
- Host ID: Identifies a device within that network.
IP addresses are categorized into five classes (A–E), with different
allocations of bits for network and host identification.
IP Address Classes Table
| Class |
First Bits |
Address Range |
Network Bits |
Host Bits |
Total Networks |
Total Hosts per Network |
CIDR Notation |
Private IP Range |
| A |
0xxx xxxx (0–127) |
1.0.0.0 – 126.255.255.255 |
8 |
24 |
2^7 = 128 (minus reserved) |
2^24 - 2 ≈ 16.7M |
/8 |
10.0.0.0/8 |
| B |
10xx xxxx (128–191) |
128.0.0.0 – 191.255.255.255 |
16 |
16 |
2^14 = 16,384 |
2^16 - 2 = 65,534 |
/16 |
172.16.0.0/12 |
| C |
110x xxxx (192–223) |
192.0.0.0 – 223.255.255.255 |
24 |
8 |
2^21 = 2,097,152 |
2^8 - 2 = 254 |
/24 |
192.168.0.0/16 |
| D (Multicast) |
1110 xxxx (224–239) |
224.0.0.0 – 239.255.255.255 |
N/A |
N/A |
N/A |
N/A |
N/A |
N/A |
| E (Reserved) |
1111 xxxx (240–255) |
240.0.0.0 – 255.255.255.255 |
N/A |
N/A |
N/A |
N/A |
N/A |
N/A |
Notes:
- Class A: The first bit must be
0.
- Class B: The first two bits must be
10.
- Class C: The first three bits must be
110.
- Class D: Used for multicast (group communications).
- Class E: Reserved for future and experimental use.
Special Reserved IP Addresses
Some IP addresses serve specific purposes and cannot be assigned to devices for regular use:
| Reserved Range |
Purpose |
127.0.0.0/8 |
Loopback (localhost) – Used for local machine testing (127.0.0.1) |
169.254.0.0/16 |
Link-local (APIPA) – Assigned when DHCP is unavailable |
255.255.255.255 |
Broadcast – Sends messages to all devices in a local network |
Private vs. Public IPs
Private IP addresses (from Class A, B, and C) are reserved for internal
network use. These addresses are not routable on the public internet and
require NAT (Network Address Translation) to connect to external networks.
| Private IP Block |
CIDR Notation |
Common Use |
10.0.0.0 – 10.255.255.255 |
/8 |
Large private networks (e.g., ISPs, enterprises) |
172.16.0.0 – 172.31.255.255 |
/12 |
Medium-sized private networks |
192.168.0.0 – 192.168.255.255 |
/16 |
Home & small business networks |
Firewalls
Packet Filtering Router
The router is the entry and exit point to the network. We create Access
Control Lists (ACLs) to provide security based on filtering rules. An ACL is a
list of statements programmed into the router's interface.
Every router has at least two interfaces and at each interface we have an ACL in
to filter incoming packets and an ACL out to filter outgoing packets.
ACL Principles
ACLs are based on two fundamental principles:
- sequential processing
- deny all except when explicitly permitted.
The source IP address, destination IP address, type of protocol, and port number
can all be used to filter packets.
There are two types of ACLs:
- standard ACL which can permit/deny based on source IP address only
- extended ACL which can permit/deny based on the source, destination,
protocol, and port.
Standard ACL
The format for a standard ACL:
access-list <acl-number> {permit/deny} <source> [mask]
...
access-list <acl-number> {permit/deny} <source> [mask]
interface <interface-number>
ip access-group <acl-number> {in/out}
-
Rule of Thumb: Bind the ACL closest to the network being protected.
-
Deny unless explicitly permitted: If no rule matches for a given packet,
then it is dropped.
Example:
Deny traffic from 172.16.4.0 on 172.16.3.0.
Allow all other 172.16.0.0 traffic.
access-list 1 deny 172.16.4.0 0.0.0.255
access-list 1 permit 172.16.0.0 0.0.255.255
interface E0
ip access-group 3 out
Extended ACL
The format for extended ACL:
access-list <acl-id> {permit/deny} <protocol> <source> <source mask>
<destination> <destination mask> [{eq/range} <port number>]
interface <interface id>
ip access-group <acl-id> {in/out}
-
Protocols: udp, tcp, icmp, igmp, ip (all protocols)
-
Rule of Thumb: In some cases, bind closes to source network - this helps
reduce router processing.
-
Deny unless explicitly permitted: If no rule matches for a given packet,
then it is dropped.
Example:
Deny all FTP access and SSH access on 172.16.3.0.
Deny non 172.16.0.0 traffic on 3.0
access-list 101 deny tcp 172.16.0.0 0.0.255.255 172.16.3.0 0.0.0.255
access-list 101 deny tcp any 172.16.3.0 0.0.0.255 range 20-21
access-list 101 deny ip any 172.16.3.0 0.0.0.255 eq 22
access-list 101 permit ip 172.16.0.0 0.0.255.255 172.16.3.0 0.0.0.255
interface E0
ip access-group 101 out
Limitations
- Address spoofing can break an ACL.
- Works only up to layer 3. Some limited extensions with extended ACLs.
- Uses up router resources.
- Testing complex ACLs can be difficult.
- Filtering specific application commands not possible (e.g. HTTP GET/POST).
- Allows direct TCP connection between outside and inside networks.
Gateway Firewall
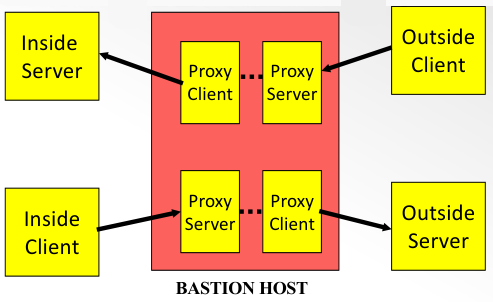
Filtering is done at the application layer, rather than the network layer.
Special gateway host called the Bastion Host (BH) acts as a relay for all
services. The BH acts as a proxy for all clients/server connections. This ensure
that there is no direct packet exchange between the private and outside network.
The BH should execute a secure version of the OS. Only essential services are
installed. Each proxy is a separate program that is independent of all other
proxies. BH can be configured to require additional authentication from the
user. Users are not allowed to log on to the BH.
Screened Host Firewall
The BH resides on the same network segment as the private network hosts and
secures the servers. Packet filtering on the router is configured to only allow
traffic to the BH. Internals machines may be permitted to have direct access or
may have to go through the BH.
This style of firewall allows for high flexibility but low security as
the BH resides along side the other machines on the same network segment.
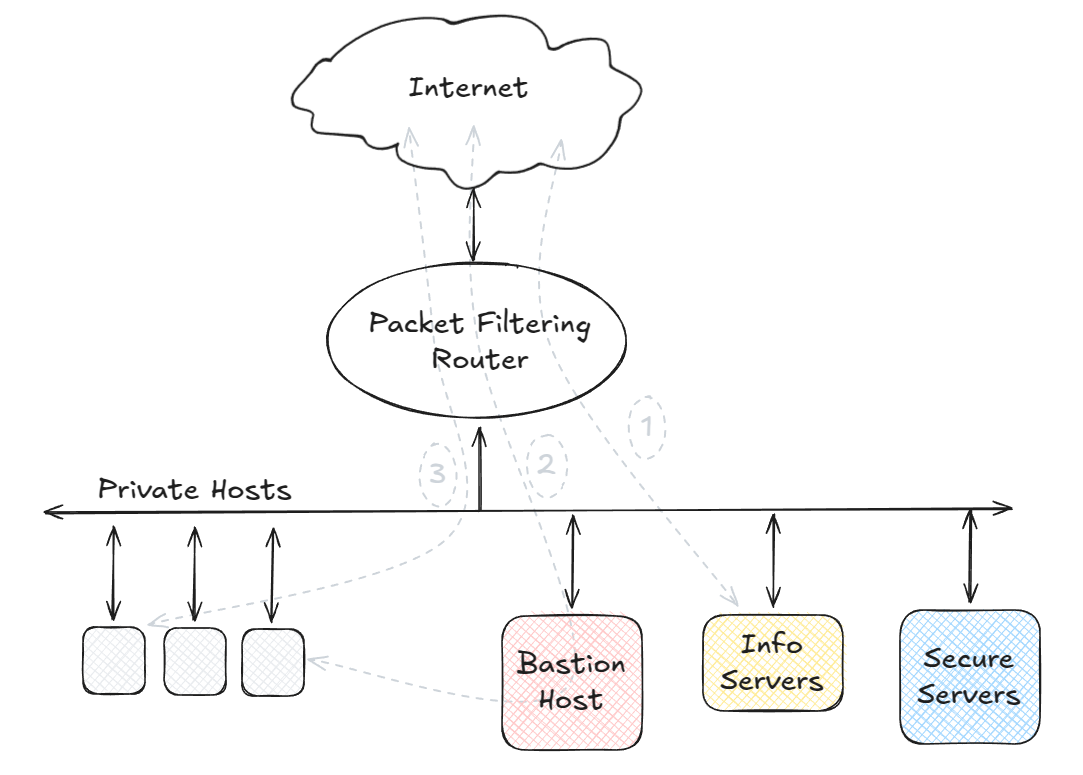
The router can be configured to allow different types of connections as shown in
the diagram:
- The outside network is permitted to directly connect to the internal
information servers.
- The private hosts can connect to the outside network by using proxies through
the BH. The outside network can access the internal servers using proxies
through the BH.
- The private hosts and the private server may be permitted to connect to the
outside network directly (without proxy though BH).
Dual Homed Gateway Firewall
The Bastion Host has two interfaces and is placed between the outside and inside
networks - acting like a router to the internal hosts. All traffic destined for
the is forced through the bastion host.
Information servers are usually placed on a separate segment outside the BH so
that outside users can access them without having to setup proxies. A packet
filtering router with ACL guides traffic to the info servers or the BH.
This provides us with high security but low flexibility as all traffic
must flow through the BH and private hosts need to use proxies to access the
info-servers.
Screened Subnet Gateway Firewall
Rather than a dual homed BH, this configuration uses two routers. The BH and
the info-servers are placed on the network segment formed between the two
routers. This network segment between the private network and the outside
network is referred to as the De-Militarized Zone (DMZ) network.
ACLs in the two routers ensure that direct transmission of traffic across the
DMZ is prohibited.
Network Address Translation (NAT)
A feature of the dual homed and screened subnet configuration is that IP
addresses of the private network need not be advertised to outside networks
(Internet). This is made possible by translating the internal or private
address to an external or public address.
This translation between internal and external IP addresses is done by a Network
Address Translator (NAT). The NAT's function is typically implemented on the
gateway firewall (BH).
The IANA has allocated the following three blocks of IP addresses for assigning
private address:
10.0.0.0 - 10.255.255.255172.16.0.0 - 172.31.255.255192.168.0.0 - 192.168.255.255
In addition to providing security, NAT is also very useful in mitigating the
problem of IP address depletion.
Static One-to-One NAT
A static one-to-one NAT assigns each internal host a unique external IP address.
The address mapping is fixed. This makes is simple to setup but it doesn't help
with IP address depletion.
This type of NAT is useful when internal servers have to be accessible from
outside networks.
Dynamic Many-to-a-Pool NAT
In a dynamic NAT, each private IP address is assigned dynamically to a public IP
address based on demand. This causes the mapping table changes periodically. A
dynamic many-to-a-pool NAT assigns a public IP address to the private address by
choosing one from the pool. This helps in reducing the number of IP addresses
used by has the disadvantage that we can only have the same number of active
clients connecting to an external network as the number of public IP addresses
available.
Dynamic Many-to-One NAT
In this case, the NAT uses port address to map internal hosts to the same
public IP address. This method is also know as NAT overloading or port address
translation (PAT). Each (private IP address, client port number) is mapped to
a (public IP address, NAT port number). This enables large number of
simultaneous connections of multiple clients outside servers.
Cryptography
A cryptosystem consists of an encryption algorithm which transforms
unconcealed data called plaintext into concealed data called ciphertext, and a
decryption algorithm which transforms the ciphertext back to the plaintext.
- Ciphers: encryption and decryption algorithms
- Keys: codes used by cipher
Symmetric Key Cryptosystems
In symmetric key cryptosystems, we the encryption and decryption algorithms use
the same shared key.
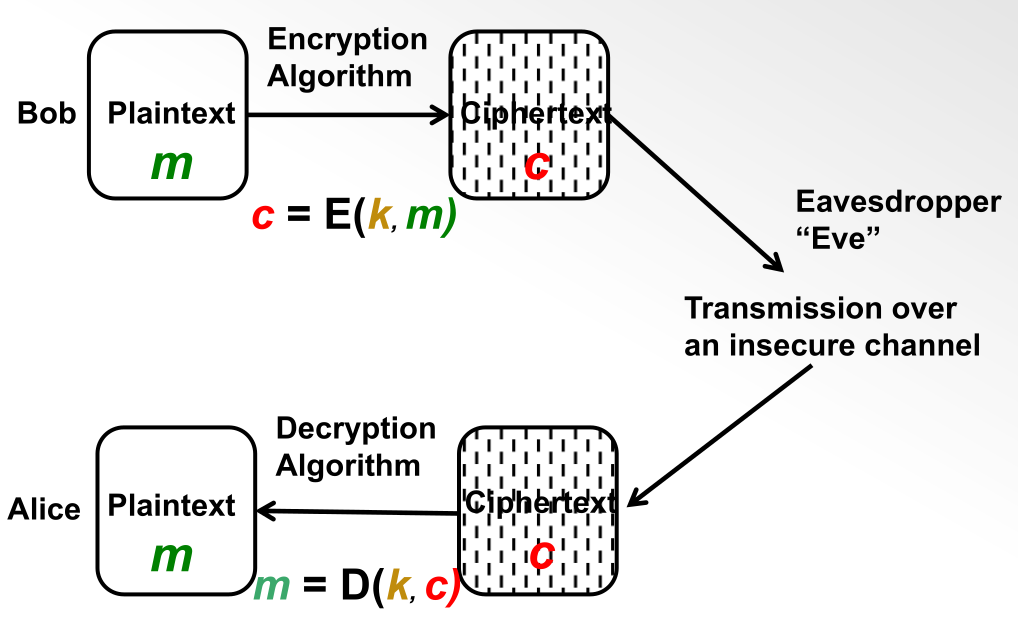
m: the plain textc: the cipher textk: the secret keyE: the encryption algorithm/functionD: the decryption algorithm/function.
The follow correctness property has to be satisfied for all valid keys \(k\) and
all valid messages \(m\):
\[
m = D(k, E(k, m))
\]
Traditional symmetric key cryptosystems have two types of ciphers --
substitution ciphers and transposition ciphers. Substitution ciphers
change the value of the plain text alphabet without changing their positions.
Transposition ciphers change the positions of the plain text without changing
their value.
Substitution Ciphers
Substitution ciphers are of two types: mono-alphabetic and poly-alphabetic.
Mono-alphabetic substitution ciphers use a fixed substitution strategy -- the
substitution does not change if the position of the plain text alphabet
changes.
Poly-alphabetic substitution ciphers use a variable substitution strategy --
the substitution of a plain text alphabet can be different depending upon its
position.
Caesar or Shift Cipher
The Caesar cipher is a mono-alphabetic cipher that simply shifts each litter of
the plain text m by k letters to the right, where k is the secret key.
X = ord("A")
def encryption(m, k):
c = ""
for char in m:
c += chr(((ord(char) - X) + k) % 26 + X)
return c
def decryption(c, k):
m = ""
for char in c:
m += chr(((ord(char) - X) - k) % 26 + X)
return m
Vigenere Cipher
The problem with mono-alphabetic substitution ciphers is that each letter is
encrypted by the same letter in every occurrence. The Vigenere is an example of
a poly-alphabetic substitution cipher.
The cipher consists of a symmetric matrix of the alphabet in where each row and
column shifts the alphabet by one position. The key is a string of letters. If
the message size is larger than the key size, the key is repeated to for a key
sequence.
Encryption is done by looking at the character at the intersection of row k[i]
and column m[i]. Decryption is done by looking at row k[i] and looking for
the column with c[i].
Playfair Cipher
The Playfair cipher is another poly-alphabetic substitution cipher. Pairs of
plain text letters are replaced by pairs of cipher text letters.
First a key matrix is produced. Suppose the secret key is SECURITY, the
letters of the key are written row-wise in a 5x5 matrix. After the key letters
are filled, the remaining letters of the alphabet are used to fill the key
matrix. The J and I letters share a single cell/box.

-
Build the key matrix but filling the matrix with the letters from the key and
filling in the remaining letters.
-
We divide the plain text into pairs of letters. Repeated letters are split
with an X or Q or that pairs don't have the same letters.
-
If the number of letters is not even, we pad with Z.
m: COME QUICKLY WE NEED HELP
>> CO ME QU IC KL YW EN EX ED LP
Now, for each pair we replace it with a new pair from the key matrix according
to the following rules:
-
If the two letters of the plain text appear in the same column, replace each
with the letter immediately below it.
-
If two letters of the plain text appear in the same row, replace each with
the letter immediately to the right of it.
-
If the two letters are not aligned in column or row, we draw a rectangle with
the two letters as the corners and then replace with the other two corners --
replacing row wise. (the opposite corner of the rectangle in the same row).
For example, EH would become UF:
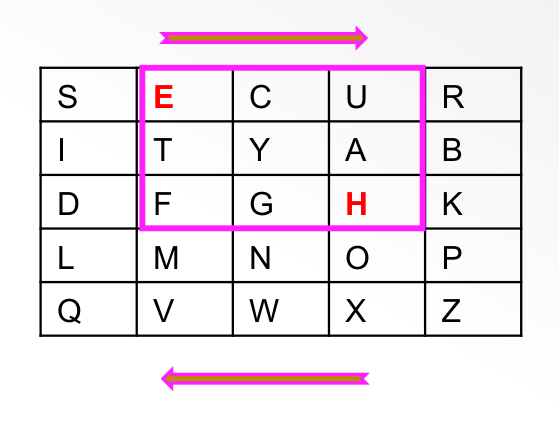
Transposition Ciphers
Rail Fence Cipher
The plain text is written in two rows, column-wise. Unfilled spots are filled by
adding space characters. The cipher text produced by reading row 1 followed by
row 2.

Matrix Transposition Cipher
The plain text is written in a matrix of n columns, row-wise. The key is a
permutation of the columns. The cipher text is generated by reading the matrix
column-wise according to the key.

Problems with Traditional Cryptosystems
In alphabetic ciphers, frequency analysis can be done to determine the plain
text. This is aided by the fact that certain letters of the English alphabet
occur more frequently than others.
They can be easily reverse engineered from a set of captured cipher texts and
knowing the corresponding plain texts.
Block Ciphers
The plain text is divided into equal sized blocks and each block is encrypted at
a time. There are three primary techniques used to perform the encryption:
substitution, permutation, looping.
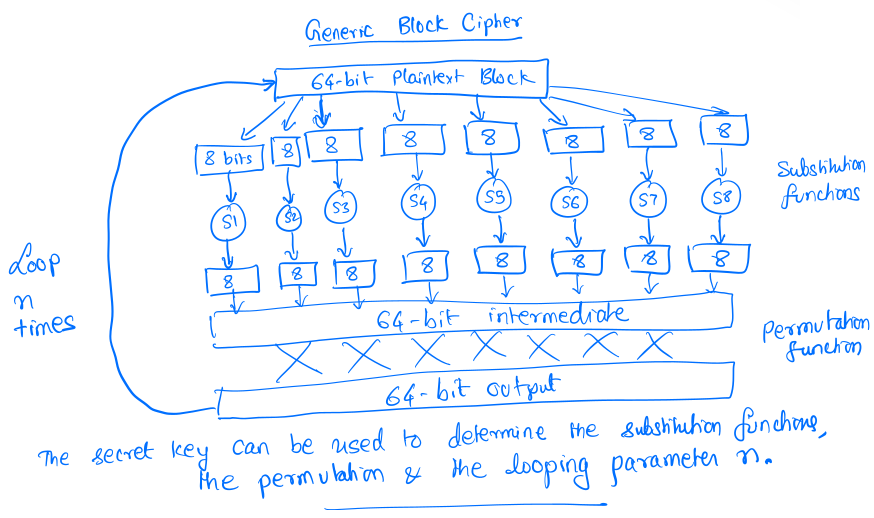
Data Encrypting Standard (DES)
Features and properties of DES:
- symmetric key cryptosystem
- block cipher
- message divided into 64-blocks
- each block encrypted in 16 rounds
- key size is
56 bits.
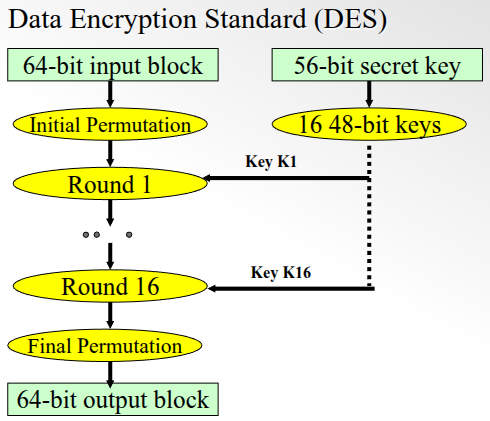
Permutations: The initial and final permutations are not derived from keys
and thus do not directly add to the security. They just make brute force reverse
engineering of the key less efficient. The initial and final permutations are
inverses of each other.
To calculate the inverse of a permutation, we just find the location of each of
the indices. For example, in the permutation below, column 1 is at 4,
therefore, the first element in the inverse is going to be 4.
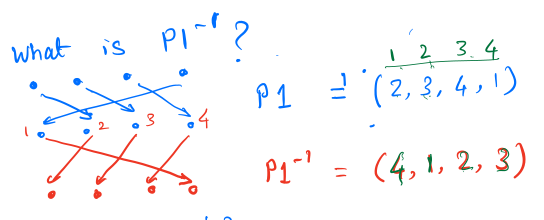
TODO: Show how the DES keys are created and how the DES algorithm works.
In 1999, DES could be brute-force cracked in about 22 hours.
Electronic Code Book (ECB) Method
When we have multiple blocks, the ECB method simple encrypts each of these
block separately/independently with the same key. However, this has the draw
back that if \(m_i = m_j\) then \(c_i = c_j\) as well. That is, identical plain text
blocks will result in identical cipher text blocks.
Cipher Block Chaining (CBC) Method
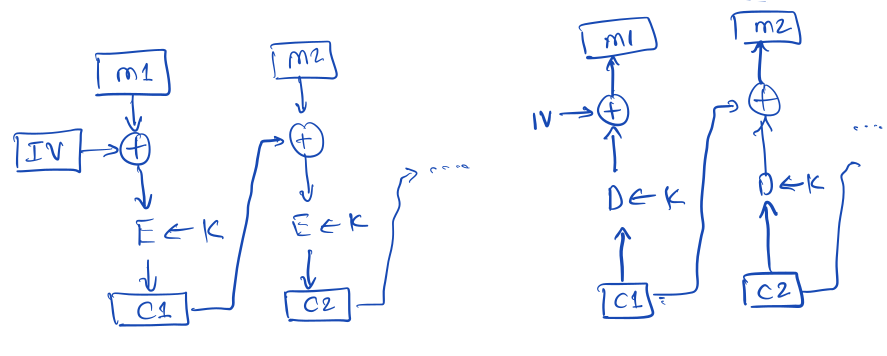
The IV is the initialization vector (a random number chosen and sent by the
sender).
The CBC method is sequential and is slower to process than ECB as we cannot
encrypt multiple blocks at the same time.
Triple DES
-
3-Key 3-DES: We run DES encryption, then decrypt, then encrypt again -- each
with its own key to get a cipher text.
-
2-Key 3-DES: We run DES encryption with \(k_1\), then decrypt with \(k_2\), and
then encrypt with \(k_1\) again.
We use EDE and not EEE because in EEE the effects of the intermediate
permutations are cancelled out since they are inverses of each other. This would
thereby reduce the brute-forcing time.
Interoperability: If we set \(k_1 = k_2 = k_3\), then 3-DES behaves like 1-DES and
can communicate with machines using 1-DES without changing the hardware.
Stream Ciphers
A stream cipher generates a continuous bit stream from a given plain text bit
stream by encrypting the plain text on a bit-by-bit basis. All stream ciphers
use pseudorandom sequence generators (PSG) to generate a key stream from a
secret key.
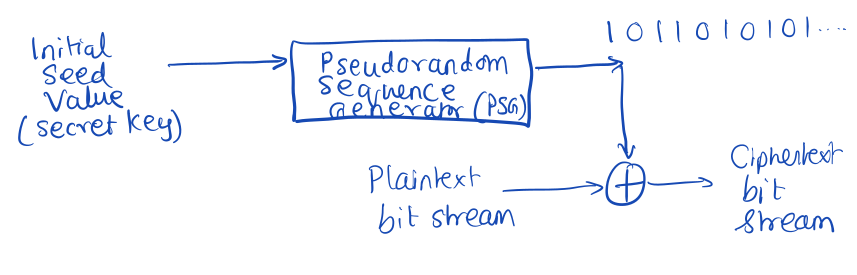
- The pseudorandom number is a statistically random bit sequence initialized by
the secret key.
- It's not mathematically random, but passes most tests for randomness.
- The plain text is XOR-ed with the pseudorandom sequence bit-by-bit to generate
the cipher text.
The pros of stream cipher include:
- lightweight - good for mobile and wireless
- high throughput - good for real-time embedded devices
- better fault tolerance - one-bit error in the input results in one-bit error
in output.
The cons of the stream cipher include:
- sender and receiver must be synchronized
- security depends on the strength of the PSG.
Linear Feedback Shift Register (LFSR)
The LFSR is used to generate pseudorandom sequences. The generic n-bit LFSR has
n shift register blocks numbered \(R_0, \dots, R_{n-1}\).
def lfsr(num_registers, taps, key, steps):
state = [int(b) for b in key]
output = []
for _ in range(steps):
feedback = 0
for t in taps:
feedback ^= state[t]
output.append(state[-1])
state = [feedback] + state[:-1]
return output
print(lfsr(8, [7, 5, 4, 3], "11001010", 20))
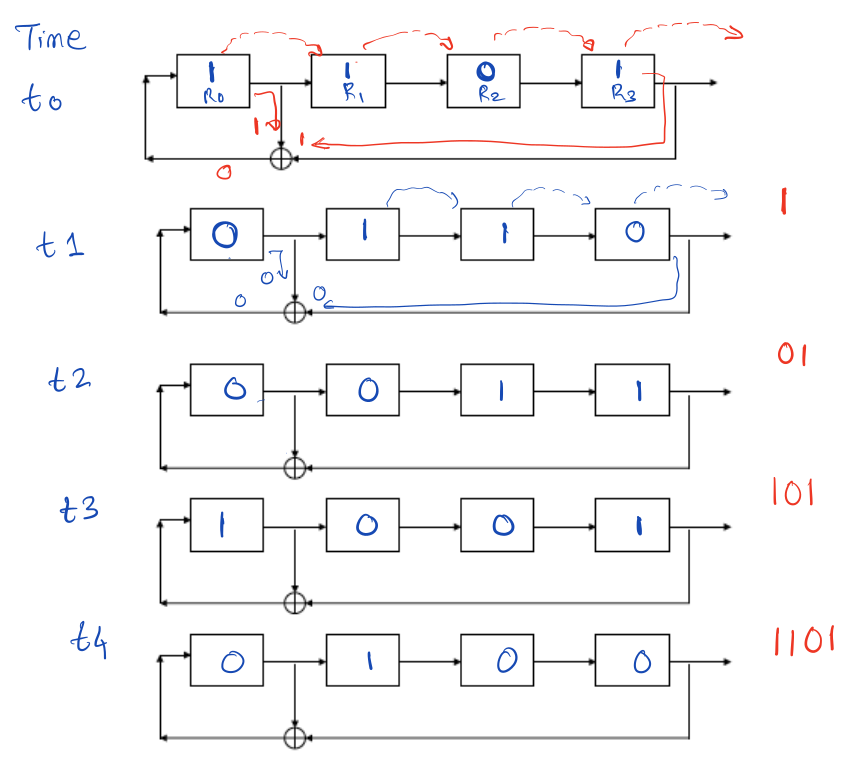
The first n bits of the pseudorandom sequence is just going to be the secret
key. To prevent this, the sender and receiver discard the first n bits from
the sequence.
The choice of tap positions is important to give maximum randomness. The tap
positions are the positions that we take and XOR to calculate the next first
bit.
Asymmetric Key Cryptosystems
With symmetric key cryptosystems, to communicate in a group of \(n\) nodes, we
need \(n(n-1)/2\) keys. They also do not provide techniques for integrity,
authentication, non-repudiation, and certification.
In asymmetric key cryptosystems, we have two separate keys for encryption and
decryption.